JSON Web Tokens (JWTs) are a well-liked method for securely transferring data between two people. JWTs are frequently used in web apps to authenticate and authorize users. They are made up of a header, a payload, and a signature. The "None" algorithm in JWTs has a major security flaw, as it can be used by attackers to get around authentication and access private data. We'll delve into the JWT None algorithm attack in this blog post and discuss how Akto can assist with its detection and mitigation.

What is JWT?
JWT is a streamlined and safe method of transferring claims between parties. Three elements make up a JWT: a preamble, a payload, and a signature. Base64 encoding is used to create the header and payload, which are then combined with a private key to create the signature. A JWT is created by the server and sent to the client, who saves it in a cookie or other local storage. The JWT is then sent by the client along with each succeeding request, enabling the server to confirm and approve the user's identity.
What is the JWT None algorithm attack?
When the algorithm defined in the header is set to "None," the JWT None algorithm attack takes place. When the algorithm is set to "None," no trace is produced, making it possible for the payload to be changed covertly. Attackers may use this flaw to their advantage by intercepting JWTs and changing the content. Due to the lack of a signature, the server will recognize the modified payload as legitimate, enabling the attacker to access confidential data or assume the identity of another user.
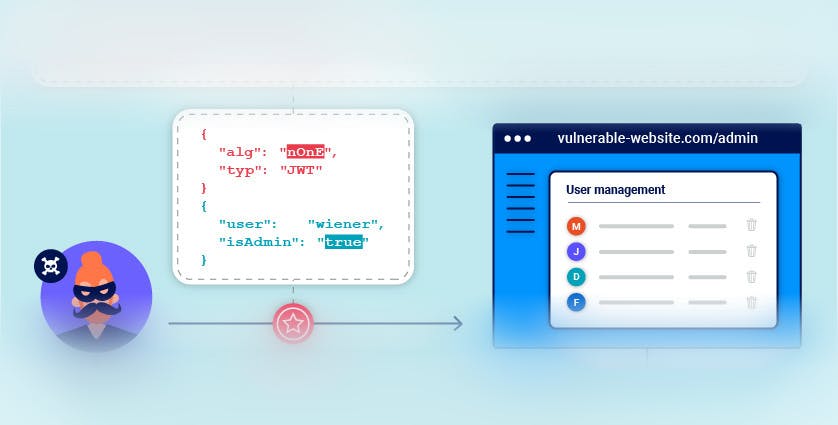
Why is the JWT None algorithm attack a big deal?
The security of your web service is seriously threatened by the JWT None algorithm attack. Your users' data may be compromised if hackers are successful in getting past authentication and accessing sensitive information, which could damage your image and trust. Furthermore, if confidential data is used, regulatory compliance may be jeopardized.
How Akto help detect and mitigate the JWT None algorithm attack?
With the aid of the potent Python library Akto, you can identify and address security flaws in your web apps. It has a JWT scanner that can identify JWTs that employ the "None" method.
Install the module with pip to use Akto:
pip install akto
Once imported, check your web application using the JWT scanner:
from akto.scanners import JWTScanner
scanner = JWTScanner()
vulnerabilities = scanner.scan("https://example.com")
Your web service will receive requests from the scan() method, which will look for JWTs that use the "None" algorithm. Akto will raise an exception and give information about the flaw if one is found.
You must make sure that your server only takes signed JWTs in order to mitigate the JWT None algorithm attack. A secure method, like HMAC or RSA, should be used to verify the signature, as well.
The following actions can be taken to stop the JWT None method attack:
Choose a safe algorithm, such as "HS256", "HS384", or "HS512."
Make sure that only verified JWTs are accepted by the server.
Sign the JWT with a safe key, and keep the key a secret.
Utilize a private algorithm, such as HMAC or RSA, to validate the signature.
In conclusion, the JWT None algorithm attack is a significant flaw that could be used by attackers to obtain confidential data without authorization. Fortunately, you can quickly find and fix this vulnerability in your web service with the aid of Akto. You can safeguard the information of your users and keep up with regulatory compliance by taking the required precautions to thwart the JWT None algorithm attack. Use a secure algorithm, only take signed JWTs, and guard the confidentiality of your signing key. Scan your web application with Akto to detect any possible security risks. Use Akto to secure your online application today.

